Grow your career in cybersecurity through our online courses. Whether you're new to the field or a seasoned professional, our cybersecurity programming offers novice to advanced courses in some of the most sought after specializations that will help you gain the skills you need for a successful career in this high-demand industry.
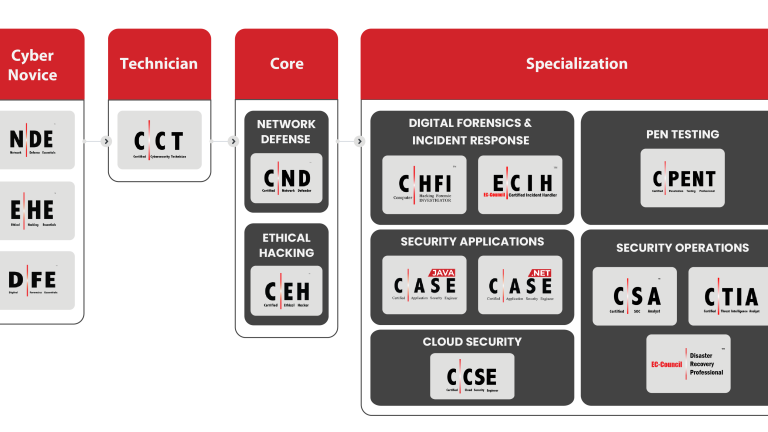
Academic certification track and stackable credentials
End User Knowledge Worker
Equip yourself with the knowledge and skills you need to begin your cybersecurity career. Learn to protect information assets and mitigate security exposure by learning the foundations of information security threats, cryptography and encryption standards.
Tuition: $315 (includes all fees and taxes)
Course Details
This course provides individuals with the necessary knowledge and skills to protect their information assets. You will learn the fundamentals of various computer and network security threats such as identity theft, credit card fraud, phishing, virus and backdoors, emails hoaxes, loss of confidential information, hacking attacks, and social engineering. The course outline includes:
- Introduction to Data Security
- Securing Operating Systems
- Malware and Antivirus
- Internet Security
- Security on Social Networking Sites
- Securing Email Communications
- Securing Mobile Devices
- Securing Cloud
- Securing Network Connections
- Data Backup and Disaster Recovery
- Securing IoT Devices and Gaming Consoles
- Secure Remote Working
Learn more about Certified Secure Computer User

Tuition: $1,420 (includes all fees and taxes)
Course Details
This course introduces professionals and students to the field of cryptography. The participants will learn the foundations of modern symmetric and key cryptography including the details of algorithms such as Feistel Functions, DES, and AES. The course outline includes:
- Introduction and History of Cryptography
- Symmetric Cryptography and Hashes
- Number Theory and Asymmetric Cryptography
- Applications of Cryptography
- Cryptanalysis
Learn more about Certified Encryption Specialist
Cyber Novice Level
Prepare for entry-level positions in the cybersecurity field. Completing one or more of these novice level courses may also help students narrow down their future career path and certification track.
Tuition: $169 (includes all fees and taxes)
Course Details
This is a novice-level course that is designed to teach the fundamental elements of digital forensics; one of three core cybersecurity disciplines. Completion of this course will prepare you for an entry-level position in cybersecurity and serve as a foundation for further certifications in digital forensics. The course outline includes:
- Computer Forensics Fundamentals
- Computer Forensics Investigation Process
- Understanding Hard Disks and File Systems
- Data Acquisition and Duplication
- Defeating Anti-forensics Techniques
- Windows Forensics
- Linux and Mac Forensics
- Network Forensics
- Investigating Web Attacks
- Dark Web Forensics
- Investigating Email Crimes
- Malware Forensics
Learn more about Digital Forensics Essentials

Tuition: $169 (includes all fees and taxes)
Course Details
This is a novice-level course that is designed to teach the fundamental elements of ethical hacking and penetration testing. Completion of this course will prepare you for an entry-level position in cybersecurity and serve as a foundation for further certifications in ethical hacking. The course outline includes:
- Information Security Fundamentals
- Ethical Hacking Fundamentals
- Information Security Threats and Vulnerabilities
- Password Cracking Techniques and Countermeasures
- Social Engineering Techniques and Countermeasures
- Network Level Attacks and Countermeasures
- Web Application Attacks and Countermeasures
- Wireless Attacks and Countermeasures
- Mobile Attacks and Countermeasures
- IoT and OT Attacks and Countermeasures
- Cloud Computing Threats and Countermeasures
- Penetration Testing Fundamentals
Learn more about Ethical Hacking Essentials

Tuition: $169 (includes all fees and taxes)
Course Details
This is a novice-level course that is designed to teach the fundamental elements of network defense; one of three core cybersecurity disciplines. Completion of this course will prepare you for an entry-level position in cybersecurity and serve as a foundation for further certifications in network defense. The course outline includes:
- Network Security Fundamentals
- Identification, Authentication, and Authorization
- Network Security Controls – Administrative Controls, Physical Controls, and Technical Controls
- Virtualization and Cloud Computing
- Wireless Network Security
- Mobile Device Security
- loT Device Security
- Cryptography and PKI
- Data Security
- Network Traffic Monitoring
Learn more about Network Defense Essentials

Technician Level
Once you have your bearings in the cybersecurity field, grow your career through a technician-level course that will enhance your skills and prepare you for a variety of careers, including:
- Help Desk Technician
- Cybersecurity Technician
- Technical Support Specialist
- It Support Specialist
- Desktop Support Technician
Tuition: $1,115 (includes all fees and taxes)
Course Details
This is an entry-level course that will cover the fundamental concepts of cybersecurity required to perform core security functions. You'll be equipped with the knowledge and skills to build efficient security strategies during the development of systems, networks and data centres. You'll also be prepared to monitor, detect, investigate and respond to evolving information security threats. The course outline includes:
- Information Security Threats and Vulnerabilities
- Information Security Attacks
- Network Security Fundamentals
- Identification, Authentication, and Authorization
- Network Security Controls – Administrative Controls
- Network Security Controls – Physical Controls
- Network Security Controls – Technical Controls
- Network Security Assessment Techniques and Tools
- Business Continuity and Disaster Recovery
- Application Security
- Virtualization and Cloud Computing
- Wireless Network Security
- Mobile Device Security
- IoT and OT Security
- Cryptography
- Data Security
- Network Troubleshooting
- Network Traffic Monitoring
- Network Logs Monitoring and Analysis
- Incident Response
- Computer Forensics
- Risk Management
Learn more about the Cybersecurity Technician course

Core Level
Core certifications are intermediate-level courses designed to hone your skills and learn complex network defense and hacking strategies. At this level, you can choose to specialize in defending a network or hacking.
Intermediate-level career opportunities include:
- Network Administrator
- Network Engineer
- Network Defense Technician
- Network Defense Analyst
- Information Security Officer
- Certified Ethical Hacker
Tuition: $1,525 (includes all fees and taxes)
Course Details
Certified Network Defender is the world’s most advanced network defense course that covers 14 of the most current network security domains any individuals will ever want to know when they are planning to protect, detect, and respond to the network attacks. The course contains hands-on labs, based on major network security tools and to provide network administrators real world expertise on current network security technologies and operations. The course outline includes:
- Computer Network and Defense Fundamentals
- Network Security Threats, Vulnerabilities, and Attacks
- Network Security Controls, Protocols, and Devices
- Network Security Policy Design and Implementation
- Physical Security
- Host Security
- Secure Firewall Configuration and Management
- Secure IDS Configuration and Management
- Secure VPN Configuration and Management
- Wireless Network Defense
- Network Traffic Monitoring and Analysis
- Network Risk and Vulnerability Management
- Data Backup and Recovery
- Network Incident Response and Management
Learn more about Certified Network Defender

Tuition: $2,055 (includes all fees and taxes)
Course Details
Certified Ethical Hacker is the world’s most advanced certified ethical hacking course that covers 20 of the most current security domains you'll need to know when planning to enhance the information security posture of an organization. The accredited course provides the advanced hacking tools and techniques used by hackers and information security professionals. The course outline includes:
- Introduction to Ethical Hacking
- Footprinting and Reconnaissance
- Scanning Networks
- Enumeration
- Vulnerability Analysis
- System Hacking
- Malware Threats
- Sniffing
- Social Engineering
- Denial-of-Service
- Session Hijacking
- Evading IDS, Firewalls, and Honeypots
- Hacking Web Servers
- Hacking Web Applications
- SQL Injection
- Hacking Wireless Networks
- Hacking Mobile Platforms
- IoT Hacking
- Cloud Computing
- Cryptography
Learn more about Certified Ethical Hacker

Specialization Level
As an experienced Network Defender or Ethical Hacker, these courses will give you the knowledge and skills you need to grow your career to the highest level.
You may choose to specialize in one of five core areas, including Digital Forensics and Incident Response (Computer Hacking Forensics Investigator or Certified Incident Handler course), Security Applications (Certified App Security Engineer.JAVA or .NET course), Cloud Security (Certified Cloud Security Engineer course), Penetration Testing (Certified Penetration Testing Professional course) or Security Operations (Certified Security Operations Centre Analyst, Certified Threat Intelligence Analyst or Disaster Recovery Professional course).
Completion of any of these courses will prepare you to work with organizations that require the highest level of cybersecurity protection. Specialization level career paths include:
- Hacking Forensics Investigator
- Disaster Recovery
- Incident Handler
- Threat Intelligence
- Security Operations Analyst
- Chief Information Security Officer
- Security Auditor
- Certified App Security Engineer
- Network Security Analyst
- Certified Penetration Tester
- Threat Analyst
Tuition: $1,970 (includes all fees and taxes)
Course Details
CHFI is a comprehensive course covering major forensic investigation scenarios, enabling students to
acquire hands-on experience. The program provides a strong baseline knowledge of key concepts and practices in the digital forensic domains relevant to today’s organizations. CHFI provides a firm grasp on the domains of digital forensics. The course outline includes:
- Computer Forensics in Today’s World
- Computer Forensics Investigation Process
- Understanding Hard Disks and File Systems
- Data Acquisition and Duplication
- Defeating Anti-Forensics Techniques
- Operating System Forensics
- Network Forensics
- Investigating Web Attacks
- Database Forensics
- Cloud Forensics
- Malware Forensics
- Investigating Email Crimes
- Mobile Forensics
- Forensics Report Writing and Presentation
Learn more about Computer Hacking and Forensic Investigator

Tuition: $1,420 (includes all fees and taxes)
Course Details
This course is designed to provide the fundamental skills to handle and respond to the computer
security incidents in an information system. The course addresses various underlying principles and techniques for detecting and responding to current and emerging computer security threats.
The comprehensive training program will make students proficient in handling as well as responding to
various security incidents such as network security incidents, malicious code incidents and insider attack
threats. The course outline includes:
- Introduction to Incident Response and Handling
- Risk Assessment
- Incident Response and Handling Steps
- CSIRT
- Handling Network Security Incidents
- Handling Malicious Code Incidents
- Handling Insider Threats
- Forensic Analysis and Incident Response
- Incident Reporting
- Incident Recovery
- Security Policies and Laws
Learn more about Certified Incident Handler
Tuition: $2,735 (includes all fees and taxes)
Course Details
The key philosophy behind the CPENT is simple: a penetration tester is as good as their skills, that's why we urge you to go beyond kali, and go beyond tools.
The CPENT range, where our penetration testers gain real world skills, is designed to provide challenges across every level of the attack spectrum. The range contains multiple layers of network segmentation, and once access is gained in one segment, the latest pivoting techniques are required to reach the next segment. Many of the challenges will require outside-the-box thinking and customization of scripts and exploits to get into the innermost segments of the network. The key to be a highly skilled penetration tester is to go up against a variety of targets that are configured in a variety of ways. The CPENT consists of entire network segments that replicate an enterprise network - this is not a computer game simulation; this is an accurate representation of an enterprise network that will present the latest challenges to the pen tester. The targets and segments are progressive in nature, once you get into one machine and or segment, the next one will challenge you even more.
At the end of the course, you'll also have a chance to attain 2 certifications with one exam.
Learn more about Certified Penetration Testing Professional

Tuition: $1,420 (includes all fees and taxes)
Course Details
The CASE Java program is designed to be a hands-on, comprehensive application security training course
that will help software professionals create secure applications. It trains software developers on the critical security skills and knowledge required throughout a typical software development life cycle (SDLC), focusing on the importance of the implementation of secure methodologies and practices required in today’s insecure operating environment. The course outline includes:
- Understanding Application Security, Threats and Attacks
- Security Requirements Gathering
- Secure Application Design and Architecture
- Secure Coding Practices for Input Validation
- Secure Coding Practices for Authentication and Authorization
- Secure Coding Practices for Cryptography
- Secure Coding Practices for Session Management
- Secure Coding Practices for Error Handling
- Static and Dynamic Application Security Testing (SAST & DAST)
- Secure Deployment and Maintenance
Learn more about Certified App Security Engineer (JAVA)

Tuition: $1,420 (includes all fees and taxes)
Course Details
This course goes beyond the guidelines on secure coding practices and includes secure requirement gathering, robust application design and handling security issues in post development phases of application development. This makes CASE one of the most comprehensive certifications for secure software development on the market today. It’s desired by software application engineers, analysts, testers globally, and respected by hiring authorities. The hands-on training program encompasses security activities involved in all phases of the Secure Software Development Life Cycle (SDLC): planning, creating, testing and deploying an application.
Learn more about the Certified App Security Engineer (.net) course

Tuition: $1,420 (includes all fees and taxes)
Course Details
This course is the first step to joining a security operations center (SOC). It is engineered for current and aspiring Tier I and Tier 11 SOC analysts to achieve proficiency in performing entry-level and intermediate-level operations. CSA is a training and credentialing program that helps the candidate acquire trending and in-demand technical skills through instruction by some of the most experienced trainers in the industry. The program focuses on creating new career opportunities through extensive, meticulous knowledge with enhanced level capabilities for dynamically contributing to a SOC team.
The 3-day course covers the fundamentals of SOC operations, before relaying the knowledge of log management and correlation, SIEM deployment, advanced incident detection and incident response. Additionally, the candidate will learn to manage various SOC processes and collaborate with CSIRT at the time of need.
Learn more about Certified Security Operations Centre Analyst
Tuition: $1,420
Course Details
This course uses a holistic approach, covering concepts from planning the threat intelligence project to building a report to disseminating threat intelligence. These concepts are highly essential while building effective threat intelligence and, when used properly, can secure organizations from future threats or attacks. You'll learn all the stages involved in the Threat Intelligence Life Cycle. This attention to a realistic and futuristic approach makes this course one of the most comprehensive threat intelligence certifications on the market today.
Learn more about Certified Threat Intelligence Analyst

Tuition: $1,985 (includes all fees and taxes)
Course Details
This course identifies vulnerabilities and takes appropriate countermeasures to prevent and mitigate
failure risks for an organization. It also provides the networking professional a foundation in disaster
recovery course principles, including preparation of a disaster recovery plan, assessment of risks in the
enterprise, development of policies and procedures, an understanding of the roles and relationships of
various members of an organization, implementation of a plan and recovering from a disaster. The course outline includes:
- Introduction to Disaster Recovery and Business Continuity
- Business Continuity Management (BCM)
- Risk Assessment
- Business Impact Analysis (BIA)
- Business Continuity Planning (BCP)
- Data Backup Strategies
- Data Recovery Strategies
- Virtualization-Based Disaster Recovery
- System Recovery
- Centralized and Decentralized System Recovery
- Disaster Recovery Planning Process
- BCP Testing, Maintenance, and Training
Learn more about Certified Disaster Recovery Professional

Tuition: $1,525 (includes all fees and taxes)
Course Details
This is a vendor-neutral course that focuses on cloud security practices, technologies, frameworks, and principles to deliver a well-balanced mix of the theoretical and practical skills you need to become a cloud security expert. The course outline includes:
- Introduction to Cloud Security
- Platform and Infrastructure Security in the Cloud
- Application Security in the Cloud
- Data Security in the Cloud
- Operation Security in the Cloud
- Penetration Testing in the Cloud
- Incident Detection and Response in the Cloud
- Forensics Investigation in the Cloud
- Business Continuity and Disaster Recovery in the Cloud
- Governance, Risk Management, and Compliance in the Cloud
- Standards, Policies, and Legal Issues in the Cloud
- Private, Hybrid, and Multi-Tenant Cloud Security
Learn more about the Certified Cloud Security Engineer course

Executive Level
Students who qualify for this level will focus on obtaining senior management skills which will allow those with highly technical expertise transition to the highest levels of information security executive management. Executive-level courses will focus on skills development in areas including audit management, communication, governance, employee management, strategic program development and financial expertise.
Executive level career paths include:
- Information Privacy & Security Manager
- Information Security Manager
- Chief Information Security Officer
- Chief Information Officer
Tuition: $2,725 (includes all fees and taxes)
Course Details
This certification is an industry-leading program that recognizes the real-world experience necessary
to succeed at the highest executive levels of information security. Bringing together all the components required for a C-Level positions, this course combines audit management, governance, IS controls, human capital management, strategic program development, and the financial expertise vital for leading a highly successful IS program. This certification can be the key to a successful transition to the highest ranks of information security management.
Learn more about Certified Chief Information Security Officer

More Information
- Students must be a minimum of 16 years of age to register for any certification course
- Reliable internet connection is required to access courses, labs and exams
- Start anytime - courses will be accessible to students upon payment, regardless of the time of year
- Upon purchase, you will have access to the online course and certification exam for one year and access to the labs for 6 months
- Successful completion of a course and its corresponding exam will certify you to perform the task(s) found on the spectrum of roles that compliment the certification
- The EC-Council Continuing Education Program policy indicates exams are valid for three years, and recertification requires students to obtain 120 points by attending Professional Development activities such as webinars, conferences, and competitions or projects, each worth a pre-determined number of points. EC-Council will administer and track certification maintenance. Learn more about the certification membership annual fees and FAQs at https://cert.eccouncil.org/ece-policy.html
Find Out More and Register
To learn more about the Cybersecurity courses or to register, contact Lana:
Phone: 306-463-6431
Toll-free: 1 (866) 296-2472
Email
About EC-Council
The courses are delivered in partnership with International Council of E-Commerce Consultants (EC-Council). EC-Council's sole purpose is to build and refine the cybersecurity profession globally. They help organizations, educators, governments, and individuals to address global workforce problems by developing and curating world-class cybersecurity education programs and certifications while also providing cybersecurity services to some of the largest businesses around the world. EC-Council is trusted by seven of the Fortune 10, 47 of the Fortune 100, the Department of Defense, the global intelligence community, NATO, and more than 2,000 of the best universities, colleges, and training companies worldwide. Their programs are in 140 countries and have set the bar in cybersecurity education.


